🔒DDOS
🔒DDOS
Attack Time: Depend on ur shipping option Concurrent: Depend on ur shipping option Pro tips: The more bigger concurrent the more success rate is hitting good. So don’t blame if attack under power when u insist for smaller plan and our proxies more expensive than dying over those discount deals, if u need custom timeframe and have in mind request for how many concurrent u can pm me and i will suggest u best option Our attack can be shown on ongoing order via dstats to check power of incoming attack Please check ur target urls on https://check-host.net first with or without ddos protection Normal not like Google Hosting, We do not take target down for corporates one with cheap rates. Corporate hit always required 50-100 Concurrents!
🔥In order to ensure the safety, speed and authenticity of the hacker business, please click here to read the transaction process:(Detailed transaction proces)
After the transfer is successful, please provide TXID or screenshot and send it to our customer service email, we will handle the relevant business in a timely manner.Email: anonymoushackersx@proton.me,If you want to encrypt your message, here is our pgp public key: As soon as your order is received, we’ll reply to you to confirm that we’ve already started working on it, and we’ll give you an order number with which you can track the status of your order in real time through this link: My Order.
The Payment methods and transaction processes we accept are Bitcoin Or Monero, If you have never used Bitcoin or Monero before and don’t know how it works, you can read a guide where we explain the whole process step by step. To read it, click on the following link: How to pay with Bitcoin or Monero
Knowledge
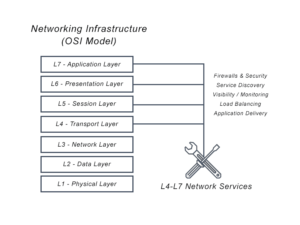
What is an L4-L7 service network?
L4-L7 service networks are application services running in these OSI layers. The L7 business network is located at the application layer and is responsible for traffic distribution. The L4 business network is called the transport layer, including TCP and UDP. L4-L7 network services provide data storage, operation, and communication services.
- We’ll get the original administrator credentials. The one that is being currently used. We won’t change anything.
- Along with the credentials, we’ll send you a free PDF document with some instructions and suggestions so that you can enter the web server with security and discretion.
- You will have a 15-day guarantee. If the administrator password changes within this time after delivery, you only have to notify us and we’ll get it again for free.
- If you want to hack two or more websites, ask us for discounts.
- If you have any questions, ask them before placing an order, not after.
- If you want to place an order as an intermediary, that is, on behalf of another person, please ask us for special conditions.
I want to place an order!
Please, make sure you have read everything before requesting a custom software development service. If you have questions or don’t understand something, ask all your questions before placing an order. If you have read, understood, and accept our service agreement completely and want to place an order for custom software development, send a message to our email: anonymoushackersx@proton.me[email protected] containing all the following 3 points that we mention below:
- Tell us that you want to hire a DDOS service.
- Confirm that you read the Service Agreement and that you agree with everything and have no doubts.
- The URL or IP address of the website that you want to DDOS.
After receiving your message, we’ll reply to confirm the start of your order. Remember that once an order has been placed, there is no way to cancel or modify it.
Related searches:
ddos website ddos Attack Script Flood attack Deformed message attack Scanning detection attacks HTTP Flood HTTP slow attack HTTPS Flood SSL DDoS attack SIP Flood zero day attack server attack Botnet traffic attack CC attack ddos attack cost Buy DDoS attack DDoS attack tools Ddos stress test What is a Gbps or Volumetric DDoS Attack What is a PPS or Network Protocol DDoS attack? What is RPS or Application Layer DDoS Attack ddos attack software